In the last post I looked at how to bring up a PostgreSQL instance in the Amazon cloud. In this post I’ll look into how to restrict access to this instance to specific IP addresses to strengthen security. If you think about moving things to the cloud you for sure want to make the stuff accessible to restricted people or systems only.
On the left side there is a “Security Groups” menu which sounds like what we want:
Seems I have to go to the EC2 console, so lets do that:
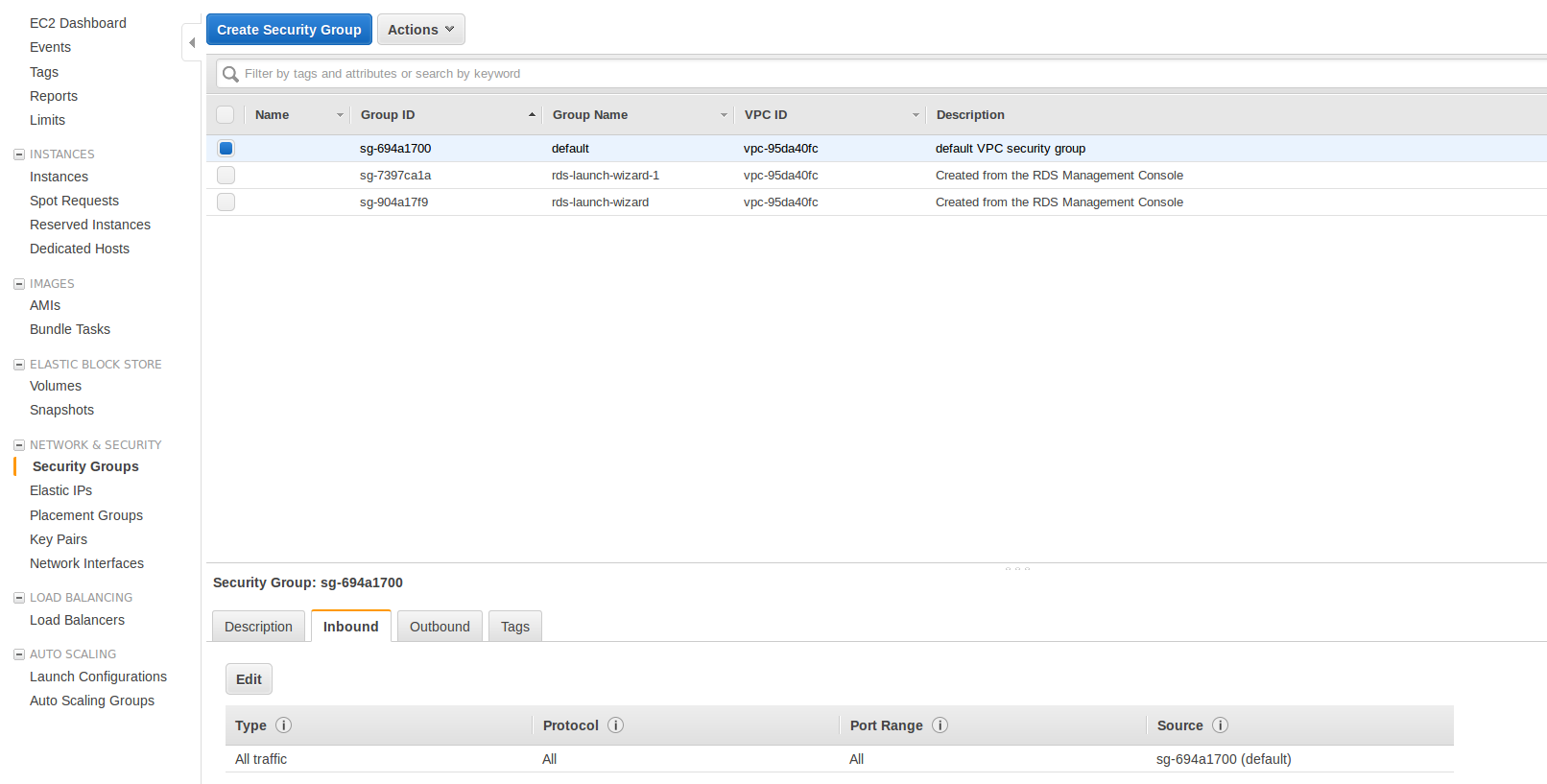
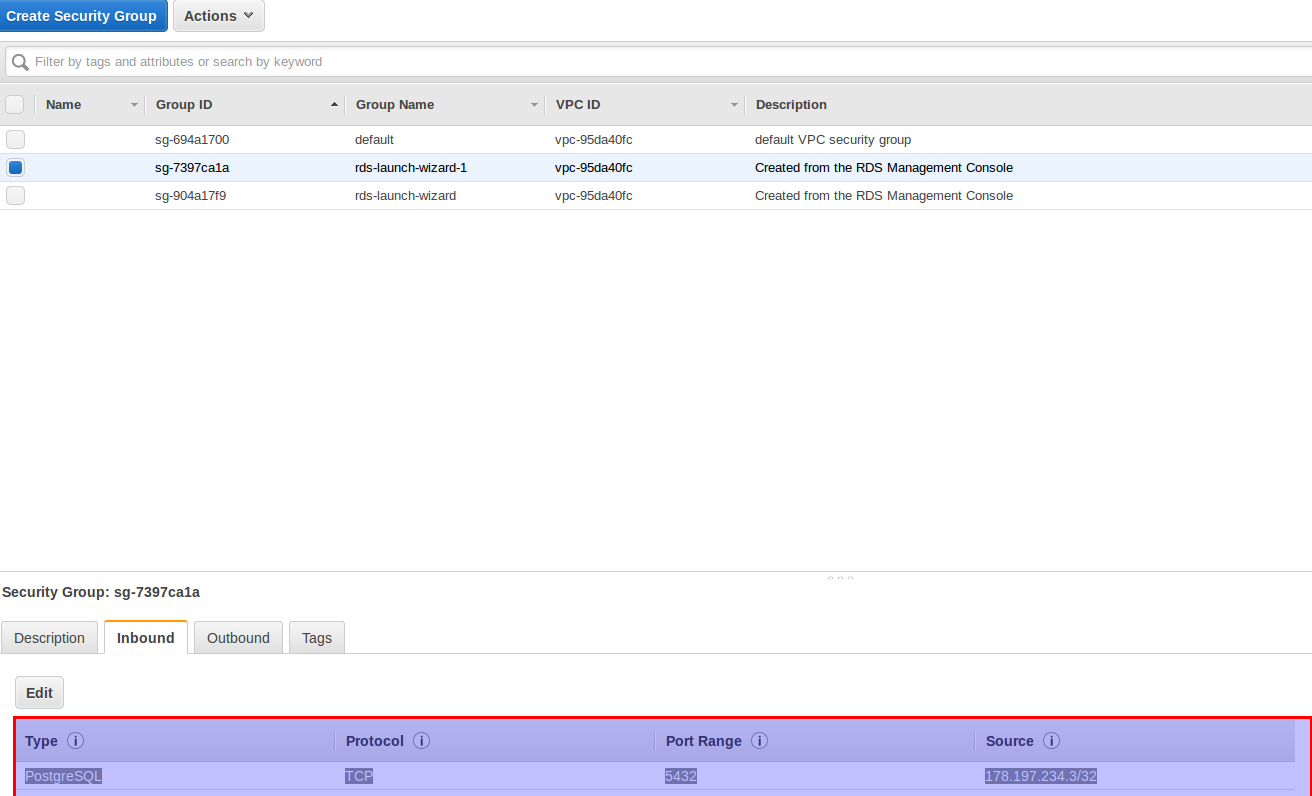
When a PostgreSQL instance is created a default security group is created with allows the machine with my local IP address to access the instance. No other clients are accepted by default:
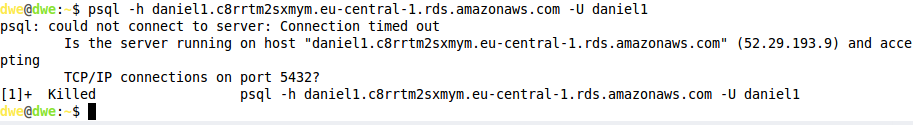
If I adjust this to something else I am no longer able to connect:
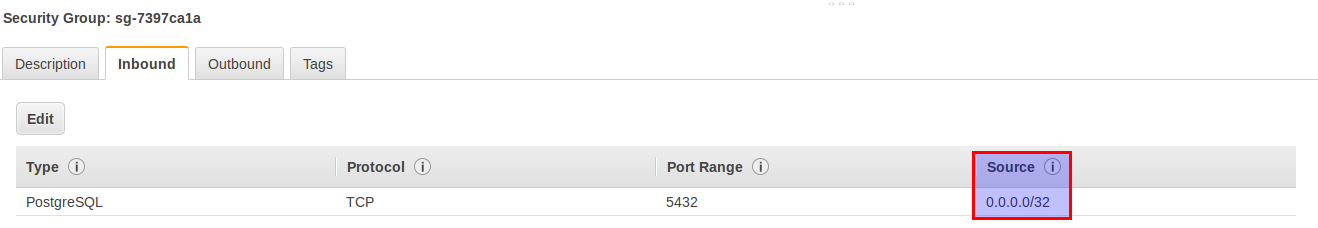
The connection attempt just hangs…
![]()
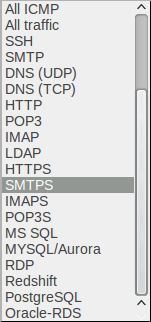
In fact these are firewall rules and you can choose among various protocols and types:
For the “source” there is the choice between a custom ip address, my own ip address and “hey, I don’t care”, which is “Anyone”:
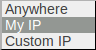
The same can be down for outbound connections:
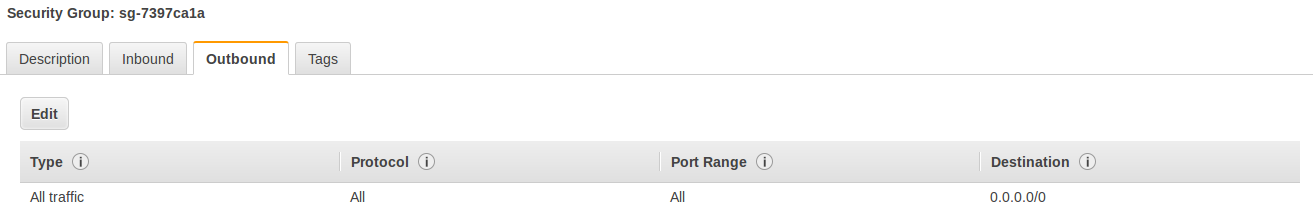
Quite easy and powerful and of course you can create new security groups:
When there are discussions about putting things into the cloud security is always a topic and it seems that Amazon did a good job here. At least for these simple tests I could prevent access to my instance very easy and fast and I am able to adjust the security settings to my needs.
In the next post I’ll look at how I can configure my PostgreSQL instance. Only when I am able to adjust the configuration for the workloads I expect the offering is really usable. Stay tuned …
![Thumbnail [60x60]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/DWE_web-min-scaled.jpg)