Most of the time when the Reports Server is configured with an Single Sign On Server, it uses the same external LDAP server as the Single Sign On Server.
In our case, we used an Oracle Access Manager as Single Sign On and an Oracle Internet Directory as LDAP server.
Of course the Fusion Middleware needs to be configured with the external LDAP server. This means an Oracle Internet Directory authenticator provider declared in the WebLogic Domain.
And an OAM Identity Assert for the Single Sign On part. But this is part to the normal Fusion Middleware configuration with SSO and external LDAP.
With this configuration in place, once the Reports Server is configured to use the SSO, the following error raises:
REP-56071: User does not exist in Id Store
This is due because Reports Server is not using the default Fusion Middleware Policy Store(jps-config.xml) but the Java Policy Store(jps-config-jse.xml). Checking this file, we can see that the Identity Store is configured to file and not to External LDAP server.
The following of this blog provides the configuration to put in place for the reports Server to take the external LDAP Server as Identity Store.
1. Configure Report Server in SSO mode
cd $DOMAIN_HOME vi ./config/fmwconfig/servers/WLS_REPORTS/applications/reports_12.2.1/configuration/rwservlet.properties <?xml version="1.0" encoding="UTF-8"?> <rwservlet xmlns_xsd="http://www.w3.org/2001/XMLSchema"> <server>rep_wls_reports_dev12cvm</server> <singlesignon>no</singlesignon> <inprocess>yes</inprocess> <webcommandaccess>L2</webcommandaccess> </rwservlet>
Change singlesignon value to yes
<?xml version="1.0" encoding="UTF-8"?> <rwservlet xmlns_xsd="http://www.w3.org/2001/XMLSchema"> <server>rep_wls_reports_dev12cvm</server> <singlesignon>yes</singlesignon> <inprocess>yes</inprocess> <webcommandaccess>L2</webcommandaccess> </rwservlet>
2. Configure the identity store for Report Server
Edit jps-config-jse.xml locate in the $DOMAIN_HOME/config/fmwconfig and add an additional service instance for the identity store
<serviceInstance name="idstore.ldap" provider="idstore.ldap.provider">
<property name="idstore.type" value="OID"/>
<property name="security.principal.alias" value="OidCredMap"/>
<property name="security.principal.key" value="OidCredKey"/>
<property name="ldap.url" value="ldap://vm01.dbi-workshop.com:3060"/>
<property name="max.search.filter.length" value="500"/>
<property name="username.attr" value="uid"/>
<extendedProperty>
<name>user.search.bases</name>
<values>
<value>cn=users,dc=delemont,dc=dbi-services,dc=com</value>
</values>
</extendedProperty>
<extendedProperty>
<name>group.search.bases</name>
<values>
<value>cn=groups,dc=delemont,dc=dbi-services,dc=com</value>
</values>
</extendedProperty>
</serviceInstance>
It must be between and and keep the other service instances
At the bottom of the same file, change the default jpsContext to use the idstore.ldap
Change:
<jpsContexts default="default">
<jpsContext name="default">
<serviceInstanceRef ref="credstore.db"/>
<serviceInstanceRef ref="keystore.db"/>
<serviceInstanceRef ref="policystore.db"/>
<serviceInstanceRef ref="audit.db"/>
<serviceInstanceRef ref="trust"/>
<serviceInstanceRef ref="pdp.service"/>
<serviceInstanceRef ref="attribute"/>
<serviceInstanceRef ref="idstore.xml"/>
<serviceInstanceRef ref="idstore.loginmodule"/>
</jpsContext>
to:
<jpsContexts default="default">
<jpsContext name="default">
<serviceInstanceRef ref="credstore.db"/>
<serviceInstanceRef ref="keystore.db"/>
<serviceInstanceRef ref="policystore.db"/>
<serviceInstanceRef ref="audit.db"/>
<serviceInstanceRef ref="trust"/>
<serviceInstanceRef ref="pdp.service"/>
<serviceInstanceRef ref="attribute"/>
<serviceInstanceRef ref="idstore.ldap"/>
<serviceInstanceRef ref="idstore.loginmodule"/>
</jpsContext>
Save and quit
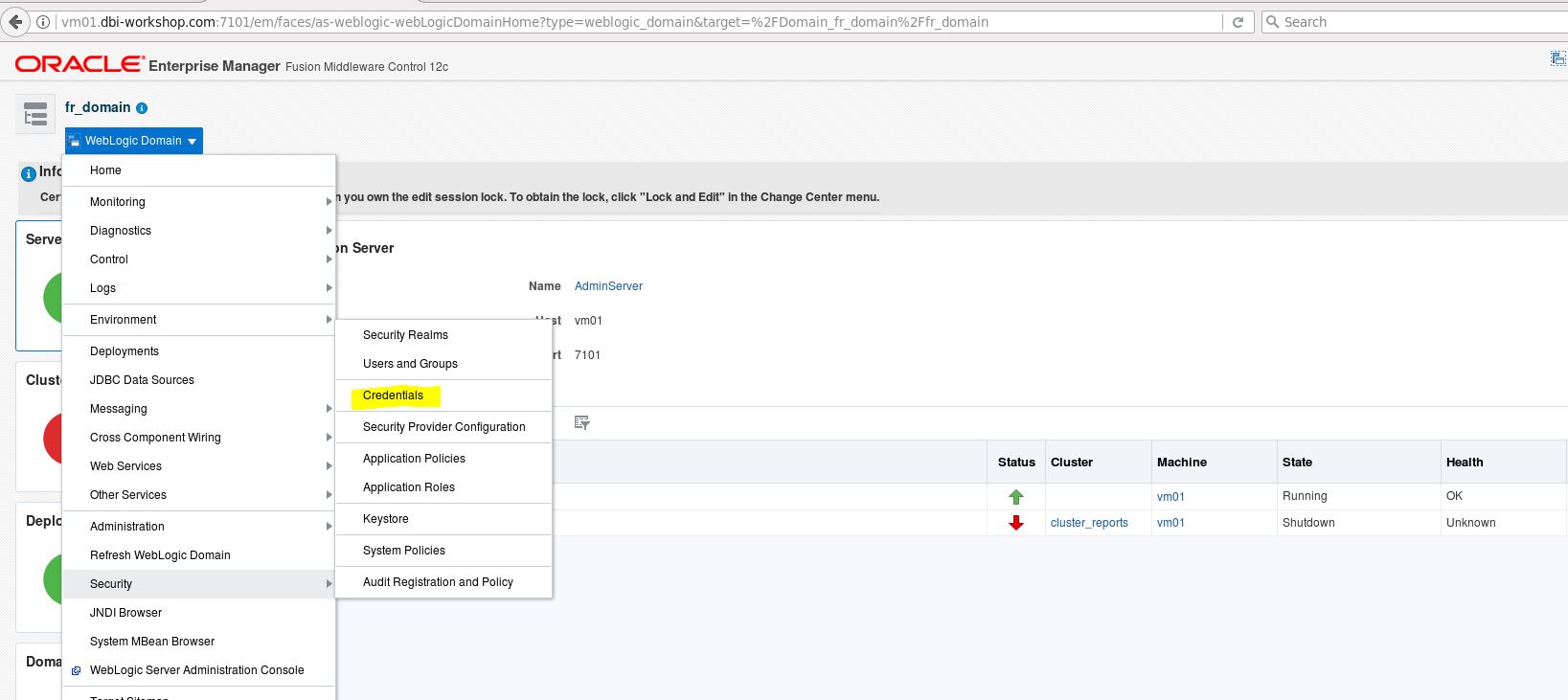
We need to create a Credential Map for this LDAP connection. Browse to the Enterprise Manager and sign in as weblogic user.
http://vm01.dbi-workshop.com:7003/em
Move to the Security -> credentials
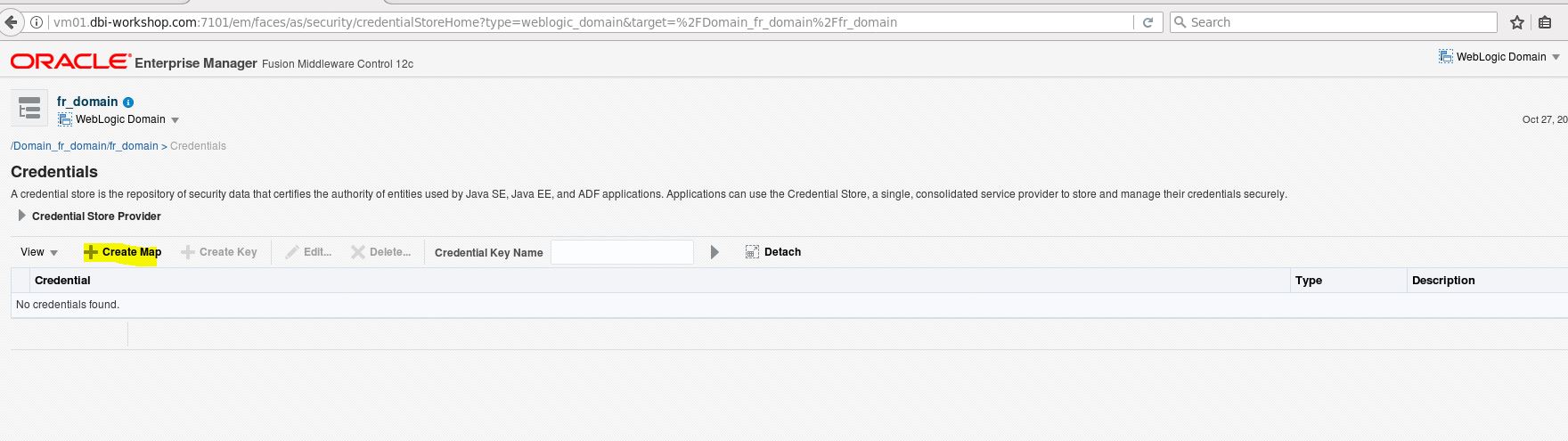
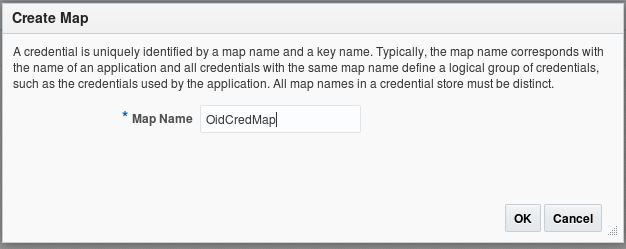
Click on Create Map and name the new credential map: OidCredMap
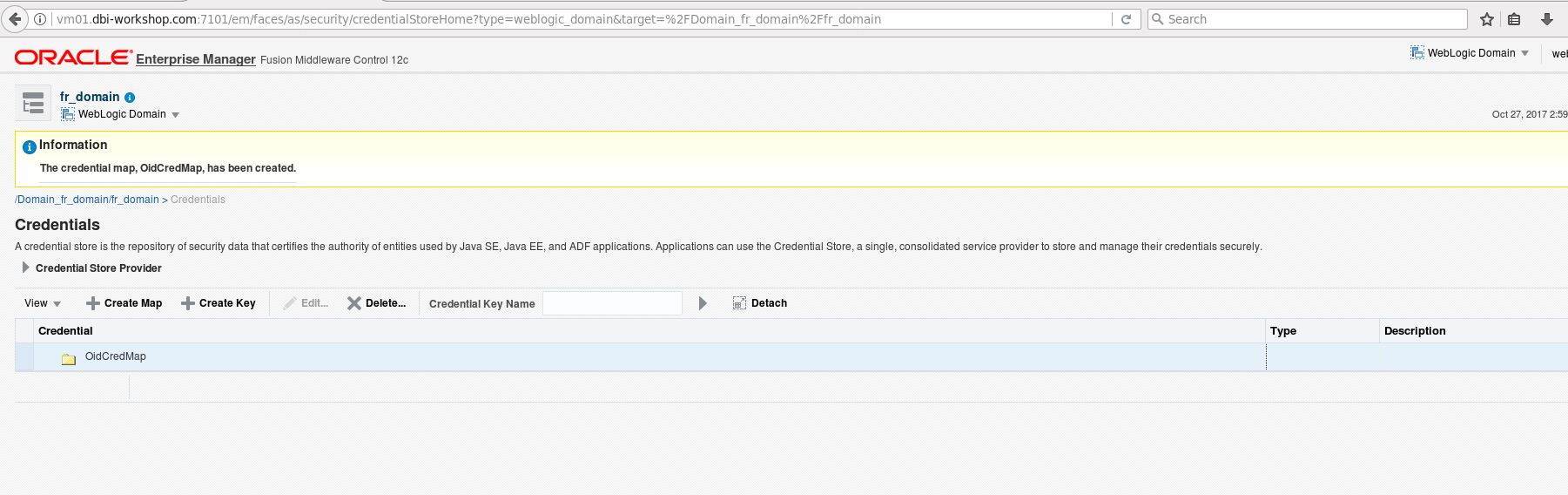
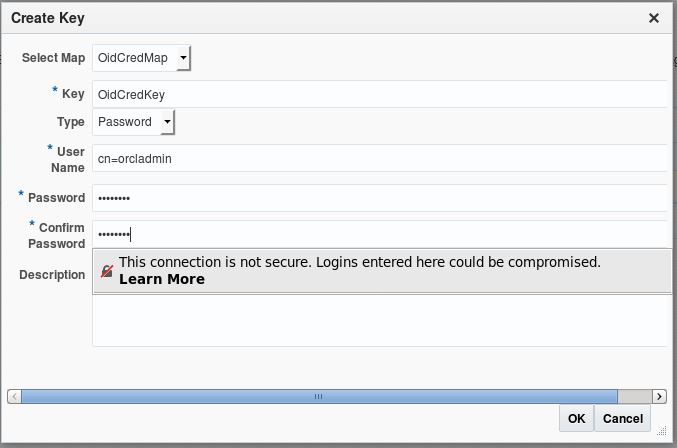
Select the credential map OidCredMap and click create key button
Key: OidCredKey
Type: Password
UserName: cn=orcladmin
Password: *****************
Confirm Password:*****************
Click OK
3. Stop and Start the full Reports WebLogic Domain
4. Configure the Report Server Security for Jobs
a. Browse to the Enterprise Manager and sign in as weblogic user
http://vm01.dbi-workshop.com:7003/em
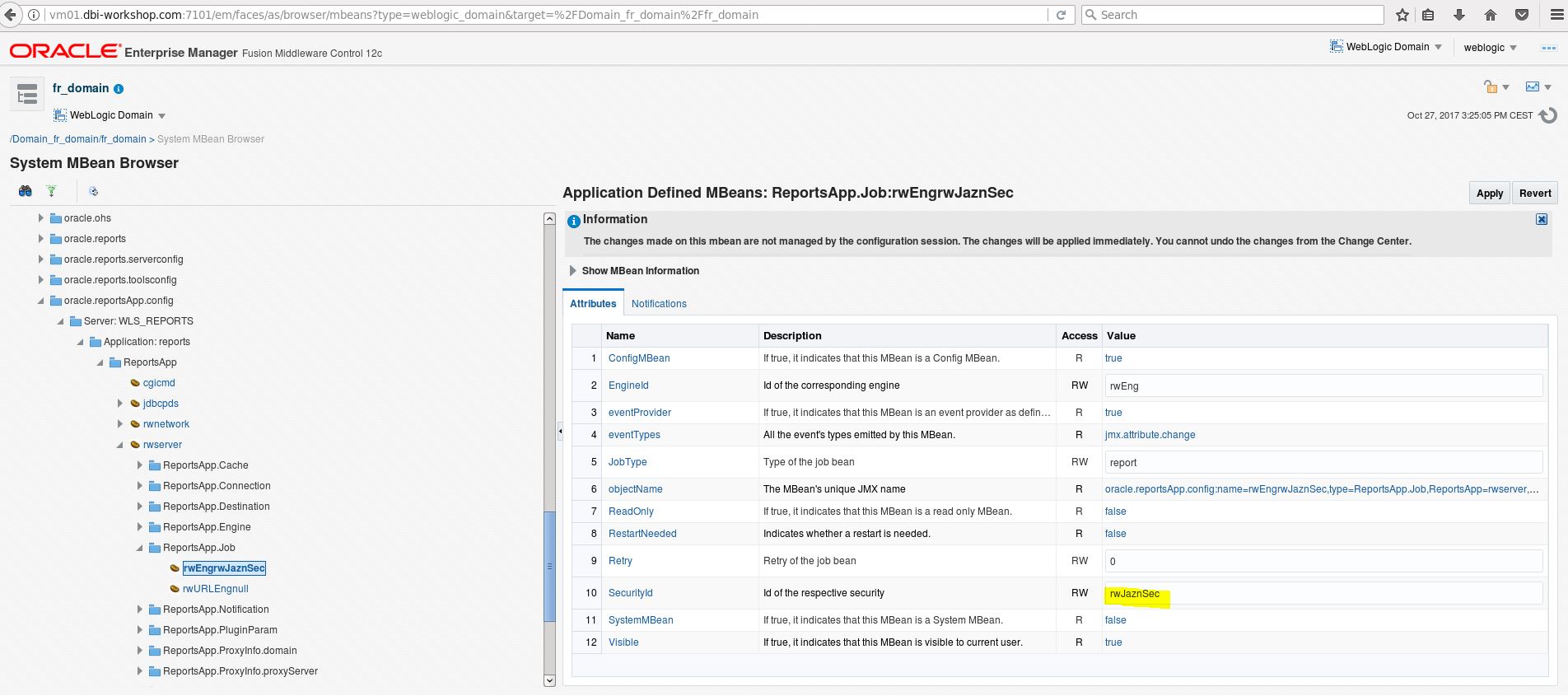
b. Navigate to the EM MBean browser Weblogic Domain > System MBean Browser
c. Navigate to reports server mbean
Folder: Application Defined MBeans
–> Folder:oracle.reportsApp.config
–> Server:<managedServername>,Application=reports, type=ReportsApp, name=rwserver, ReportsApp.Job
d. Click child mbean: rwEngrwJaznSec
e. For property securityId enter value as follows:
rwJaznSec – for OPSS based security
5. Configure the Report Server Roles
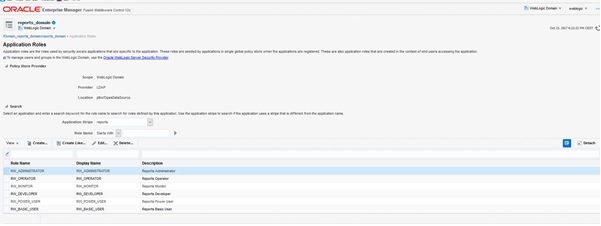
Browse to the Enterprise Manager and sign in as weblogic user
http://vm01.dbi-workshop.com:7003/em
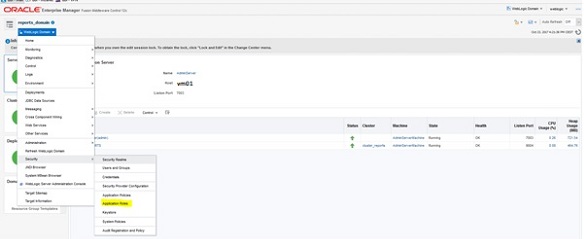
From the drop down menu, select the Security -> Application roles. The following displays
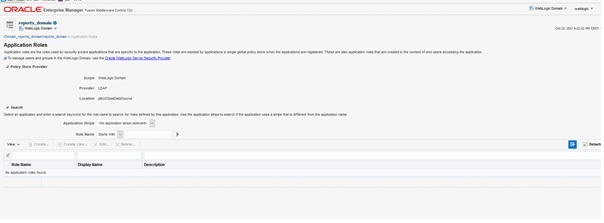
Set Application Stripe on Reports and click the search arrow
Select each role you want to add members to and click edit. In the next wizard, search for the user or group or role and click add.
![Thumbnail [60x60]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/PBR_web-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/OLS_web-min-scaled.jpg)