In this blog post, I will share my experience acquired on a customer interesting challenge which was a critical mission. The mission was not as easy as expected. On my side, all troubles that could happen to migrate an entire Identity Management – Oracle Access Manager 10g environment to 11g was exposed to me. As the challenge is completely finished, I must share my knowledge.
In this first blog post for the OAM 11gR2PS2 series, I will quickly introduce the scope of the mission. The scope, always not so easy to define and not to cross the boarder line.
I will not expose in detail the concept of Oracle Access Management 11g. You can find all needed information so easily when you google it.
Quickly, because it will be one of the concerne, the Oracle Identity Management Portfolio 11gR2 is separate in three big categories.
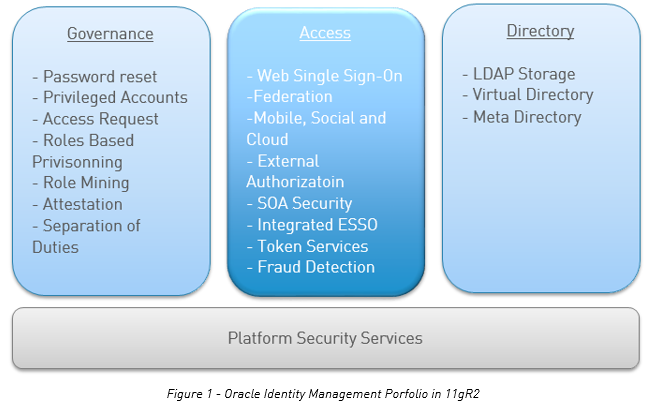
Please keep in mind that a migration from 10g to 11g can be a risk. Some of your current features can be separate and other product such as Oracle Identity Manager must be installed to. I will go through this topics when I will blog about the password self services provisioning.
So, for this OAM 11gR2PS2 series, the goal is building the following OAM environment:
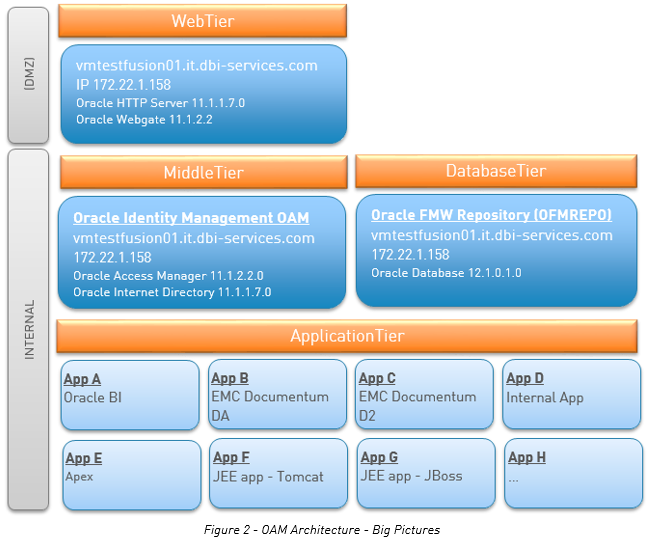
Please note that for this OAM blog serie, all the components are on the same host. I would prefer to at least separate the Oracle WebTier, the Middleware (OAM – OID) and the DatabaseTier.
The Oracle Webtier is in the real world in the DMZ behind a firewall and all other network components, to ensure the highest level of security and access restriction, in the internal network.
For an OAM environment, the webtier has an access gate module (webgate) attached to Apache and responsible of the communication with the OAM server to allow or not the access to protected resources in the application tier. Always depending on the AuthN (Authentication) and AuthZ (Authorisation) rules defined.
All this definitions in form of metadata are stored in an Oracle Database called more commonly the Oracle Fusion Middleware Repository.
All the protected resources in the application tier will have the web SSO capability when they are proxied by the WebTier. Session management and SSO token are managed by the OAM server. Emphasize the point that user accessing protected resources must be authenticated and authorized with a valid session from the a user identity store – Oracle Internet Directory (ldap directory) in our case.
The protected resources can be also synchronized to an ldap directory for their internal autorisation mechanism.
Protected applications, SSL communication termination and internal applications with LDAP synchronization:
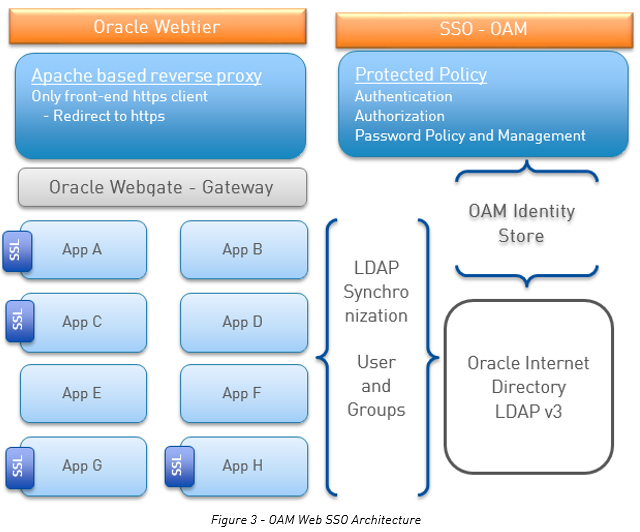
Behind the Oracle Webgate and Apache, any kind of web applications could be protected by OAM.
During this OAM 11gR2 blog post series, I will try to cover the protection of an internal JEE application, a proprietary EMC Document Documentum Administrator and D2 Client, an Apex application and possibly another kind of technology for the SSO authentication mechanism. Why not some other applications such as Alfresco, Liferay and so one. Perhaps, other SSO mechanism such as kerberos.
![Thumbnail [60x60]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/ABE_web-min-scaled.jpg)
![Thumbnail [90x90]](https://www.dbi-services.com/blog/wp-content/uploads/2022/08/OLS_web-min-scaled.jpg)